Ports and Protocols
The basic ports and protocols are displayed in the graphic below.
Ports and Protocols for a Network Device
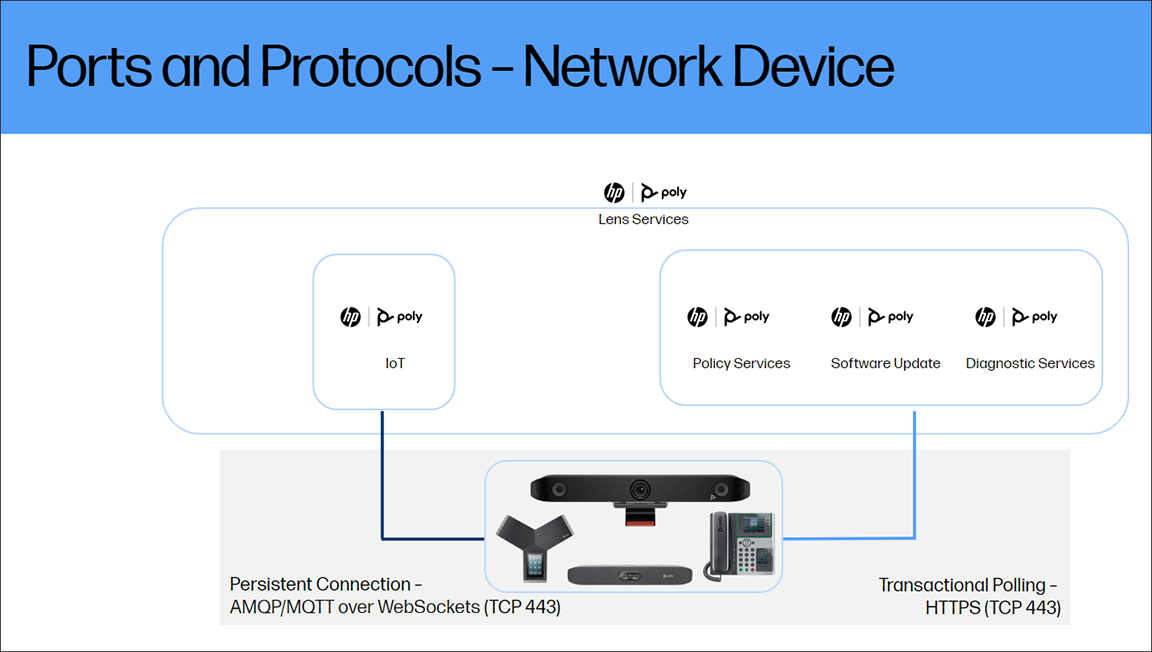
Ports and Protocols for Poly Studio Apps
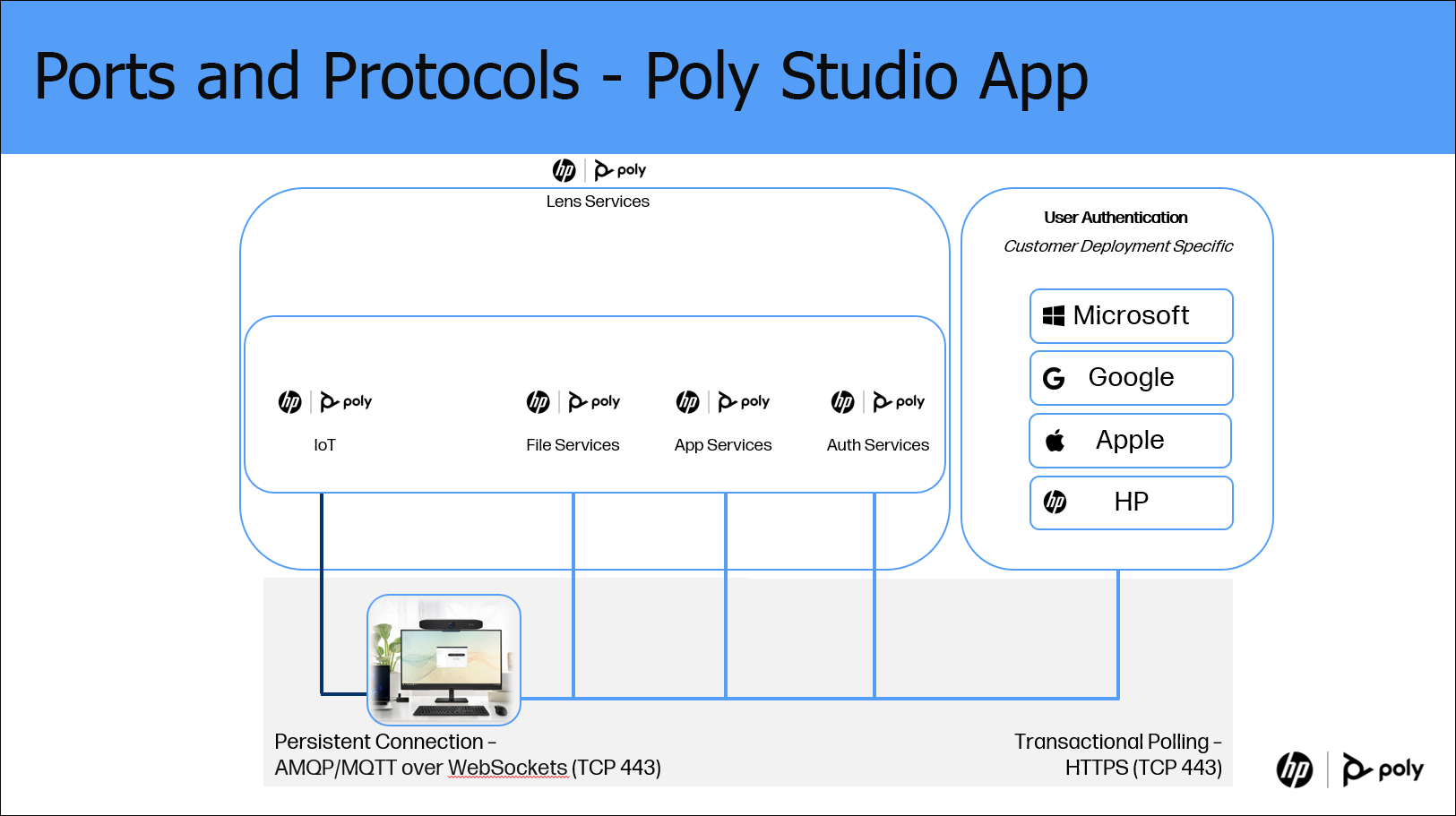
Ports and Protocols for Remote Access
Poly Studio Connection Requirements by Device Category
Note: HP Poly Studio Desktop additionally requires an HTTPS connection to Microsoft, Google, or Apple, and any corresponding Identity Providers based on your authentication provider deployment model.
- These are specific to each SSO implementation and are not provided by Poly.
Poly Lens Network Devices
| Destination | Type | Port | Purpose | Protocol | Security | Service |
|---|---|---|---|---|---|---|
| global.azure-devices-provisioning.net lens-iot-prod-iothub-eastus2.azure-devices.net lens-iot-prod-iothub2-eastus2.azure-devices.net lens-iot-prod-iothub3-eastus2.azure-devices.net lens-iot-prod-iothub4-eastus2.azure-devices.net lens‑iot‑prod‑iothub5‑eastus2.azure‑devices.net (New!) lens‑iot‑prod‑iothub6‑eastus2.azure‑devices.net (New!) eu‑lens‑iot‑prod‑iothub‑germanywestcentral.azure‑devices.net (New! for European based customers) . | TCP | 443 | Active Management (1) | AMQP / MQTT over HTTPS | TLS 1.2 | IoT |
| login.lens.poly.com api.silica-prod01.io.lens.poly.com bootstrap.silica-prod01.io.lens.poly.com | TCP | 443 | Poly Lens API & Configuration Policy | HTTPS | TLS 1.2 & TLS 1.3 | IoT |
| <uniqueid>.deviceprovisioning.dm.lens.poly.com <uniqueid>.deviceprovisioning.prod01-eu.dm.lens.poly.com (New! for European based customers) | TCP | 443 | Device Policy & Provisioning Files | HTTPS | TLS 1.2 | Policy Services |
| swupdate.lens.poly.com | TCP | 443 | Device Software | HTTPS | TLS 1.2 | Software Update |
| lensiotprodioteastus2.blob.core.windows.net | TCP | 443 | Device Uploads | HTTPS | TLS 1.2 | Diagnostic Services |
(1) HP G6 Docking Stations minimum recommended software versions:
- HP Thunderbolt 4 100W G6: 01.03.27.00
- HP Thunderbolt 4 Ultra 180W G6: 01.03.28.00
- HP Thunderbolt 4 Ultra 280W G6: 01.03.28.00
- HP USB-C 100W G6: 01.01.05.00
HP Poly Studio Apps
| Destination | Type | Port | Purpose | Protocol | Security | Service |
|---|---|---|---|---|---|---|
| global.azure-devices-provisioning.net lens-iot-prod-iothub-eastus2.azure-devices.net lens-iot-prod-iothub2-eastus2.azure-devices.net lens-iot-prod-iothub3-eastus2.azure-devices.net lens-iot-prod-iothub4-eastus2.azure-devices.net lens‑iot‑prod‑iothub5‑eastus2.azure‑devices.net (New!) lens‑iot‑prod‑iothub6‑eastus2.azure‑devices.net (New!) eu‑lens‑iot‑prod‑iothub‑germanywestcentral.azure‑devices.net (New! for European based customers) . | TCP | 443 | Policy & Cloud Settings, Device Status, Usage Telemetry | AMQP‑WS | TLS 1.2 | IoT |
| swupdate.lens.poly.com | TCP | 443 | Device Firmware & App Updates | HTTPS | TLS 1.2 | File Services |
| speedtest.lens.poly.com | TCP | 443 | Network Diagnostic Test | HTTPS | TLS 1.3 | App Services |
| lens-speedtest-04.eastus.azurecontainer.io | UDP | 8080 | Network Diagnostic Test | TCP Socket | N/A | App Services |
| login.lens.poly.com | TCP | 443 | Device User Authentication | HTTPS | TLS 1.2 | Auth Services |
| lens-auth0-silica-prod01.s3.amazonaws.com | TCP | 443 | Device User Authentication | HTTPS | TLS 1.2 | Auth Services |
| api.silica-prod01.io.lens.poly.com bootstrap.silica-prod01.io.lens.poly.com | TCP | 443 | Poly Lens API, Configuration Policy | HTTPS | TLS 1.2 | App Services |
| static.lens.poly.com | TCP | 443 | Device Images | HTTPS | TLS 1.2 | App Services |
| aadcdn.msftauth.net login.live.com | TCP | 443 | Microsoft SSO | HTTPS | TLS 1.2 | User Authentication |
| accounts.google.com lh3.googleusercontent.com | TCP | 443 | Google SSO | HTTPS | TLS 1.2 | User Authentication |
| appleid.cdn-apple.com www.apple.com | TCP | 443 | Apple SSO | HTTPS | TLS 1.2 | User Authentication |
| login3.id.hp.com | TCP | 443 | HP SSO | HTTPS | TLS 1.2 | User Authentication |
Note: Also see the System Port requirements for the device. See Device Documentation for links to the documents of supported devices.
Remote Access
Your network infrastructure should be configured to allow connections to and from the above addresses on the following ports
| Port | Protocol |
|---|---|
| 443 | TCP (TURN TLS) |
| 3478 | TCP (TURN TLS) |
| 5349 | TCP (TURN TLS) |
Servers will allocate peer relay ports in the UDP 10,000-60,000 range.
Network communication to and from the TURN servers will originate/terminate from the static IP address ranges listed below for each region. Refer to these ranges if you need to configure your local network to allow communication or apply Quality of Service routing rules to communication.
Note: Servers also use the same static IP address ranges.
| Region | Location | Server IP Address Range |
|---|---|---|
| au1 | Australia | 13.210.2.128 - 13.210.2.159, 54.252.254.64 - 54.252.254.127, 3.25.42.128 - 3.25.42.255 |
| br1 | Brazil | 18.231.105.32 - 18.231.105.63, 177.71.206.192 - 177.71.206.255, 18.230.125.0 - 18.230.125.127 |
| de1 | Germany | 52.59.186.0 - 52.59.186.31, 18.195.48.224 - 18.195.48.255, 18.156.18.128 - 18.156.18.255 |
| in1 | India | 52.66.193.96 - 52.66.193.127, 52.66.194.0 - 52.66.194.63, 3.7.35.128 - 3.7.35.255 |
| ie1 | Ireland | 52.215.253.0 - 52.215.253.63, 54.171.127.192 - 54.171.127.255, 52.215.127.0 - 52.215.127.255, 3.249.63.128 - 3.249.63.255 |
| jp1 | Japan | 13.115.244.0 - 13.115.244.31, 54.65.63.192 - 54.65.63.255, 18.180.220.128 - 18.180.220.255 |
| sg1 | Singapore | 13.229.255.0 - 13.229.255.31, 54.169.127.128 - 54.169.127.191, 18.141.157.128 - 18.141.157.255 |
| us1 | US East Coast (West Virginia) | 34.203.254.0 - 34.203.254.255, 54.172.60.0 - 54.172.61.255, 34.203.250.0 - 34.203.251.255, 3.235.111.128 - 3.235.111.255 |
| us2 | US West Coast (Oregon) | 34.216.110.128 - 34.216.110.159, 54.244.51.0 - 54.244.51.255, 44.234.69.0 - 44.234.69.127 |
Azure IP Ranges
You can download a JSON file of the IP address ranges for Public Azure here.
Note: This file is updated weekly.
AWS IP Ranges
You can download a JSON file of the IP address ranges for Public AWS here.